Spoofing attack is an alarming thing in the entire world as it has negatively affected the financial status of hundreds and thousands of peoples around the world. Such type of attack is not easier for anyone to judge or get safe from it because everything seems to be accurate and legit, which makes it miserable.
In today article, we will be going to talk about spoofing attack in detail along with discussing about the different kind of spoofing attack happening in the world. So, getting the idea about everything will help you to be safe.
WHAT IS SPOOFING ATTACK?
In general, Spoofing attack implies to the activity where a fraud person hides their actual identity and present itself like a reliable or authorized person. He/she could appear as the manager, CEO, or anything else of a company. In return, the ultimate reason of spoofing you throughout the time is to get valuable information of funds from you.
If you are not familiar about spoofing attack, you would easily give them the personal information along with transferring the funds. Later on, you will realize that the person who has called, message, email, or used any other form of communication was a fraudulent party. And now, you will disguise yourself and have nothing to do anything else.
WHAT ARE THE DIFFERENT TYPES OF SPOOFING?
Here, when we are talking about types of spoofing, it’s an alarming thing because the fraudulent party have access to different mode of communication to do the spoofing attack on you. In fact, that’s the major reason we are not talking about one or two but all types of spoofing attacks in this section for you.
CALLER ID SPOOFING:
In Caller ID Spoofing, a fraudulent party tends to call you on the mobile number. The number you will see on the screen would look attractive that is from the company or any other reliable source. The reason behind is that many fraudulent parties uses the VOIP to mask their numbers to hide their identity and represent themselves as someone else. VOIP stands for Voice over internet protocol. So, these fraudulent parties uses someone else number who is reliable to fraud you.
In a survey, it’s said that only 38% of the people who get such type of calls would identify it as the spoofing attack. Others won’t get a clue about it. Therefore, you must need to use technologies that can automatically analyze the persons who are performing caller id spoofing attack with you. That’s the only solution you could apply to safe yourself.
WEBSITE SPOOFING:
Let say you have a company website; fraudulent parties tend to do the spoofing attack on it too. All they do is to create a new website similar to yours in terms of appearance and functionalities. So, the user who tries to visit such websites assumes it as real and the fraudulent parties try to extract the sensitive information from them. In fact, your employees or customers would also affect from it. Now, the more alarming situation occurs when the fraudulent successfully spoofed your website ARP, DNS, and IP. Now, it makes the fake websites more convincing for others and will remain safe from security tools. So, the visitors who get to the fake website and didn’t realized about it, they would definitely provide them the personal information multiple times.
DNS SERVER SPOOFING:
Domain name system or DNS is used by the website owners to include an additional layer of security in their website for the visitors, customers, or employees who are accessing the website. It makes sure every secure aspect that whoever is visiting the URL, they are actually landed on the right place.
With DNS Spoofing attack, fraudulent party hijacks the URL/Name of the website by introducing the corrupt DNS information into the cache. Now, whenever a user gets into the website and enters into the corrupt DNS information, if they are in your website, the control of the user shifts to the fraudulent party. If they put any sensitive information on that corrupt DNS information, the fraudulent party can easily get all of it.
ADDRESS RESOLUTION PROTOCOL SPOOFING:
An online user who use anything on internet, it’s because of the transmit information. Different technologies collectively work with the Internet-capable devices to make everything done for the user. In technology terms, it’s called as ARP, which is Address resolution Protocol.
The fraudulent parties try to perform suspicious interactions by the ARP spoofing. In this type of spoofing attack, the fraudulent parties bypass antivirus software by mimicking the piece of data. With this, any user who got into this trap would hand over their computers in the hands of the fraudsters by linking it with the user’s IP.
EMAIL SPOOFING:
Majority of the people who are online users believes that emails are one of the safest environments for them to share information with others. Especially, the professional sectors considers it the most to send emails to others. But, one thing needs to be considering is that emails are not 100% protective at all.
In the market, skilled fraudsters are available who have the idea to perform Spoofing attack in this environment. The fraudulent parties use this communication medium to target the icebergs of the company, who are mainly the CEO’s or co-founders. They try to do the Emails in a way that looks official and if the CEO or Co-founder did any mistake, they would expose their sensitive data, which will be problematic.
BROWSER EXTENSION SPOOFING:
On Google chrome or another webs browser, there is an extension feature, which works as play store in Android mobile or iOS store in apple devices. Basically, it comes with different kind of applications that helps to give you a better experience of usage.
If we talk about extension spoofing, so you need to be careful about it as there are several extensions available on the browser that are created by the fraudulent parties. Anyone who downloads their extensions would have the higher chances of risks to share their information with them and that would negatively impact them.
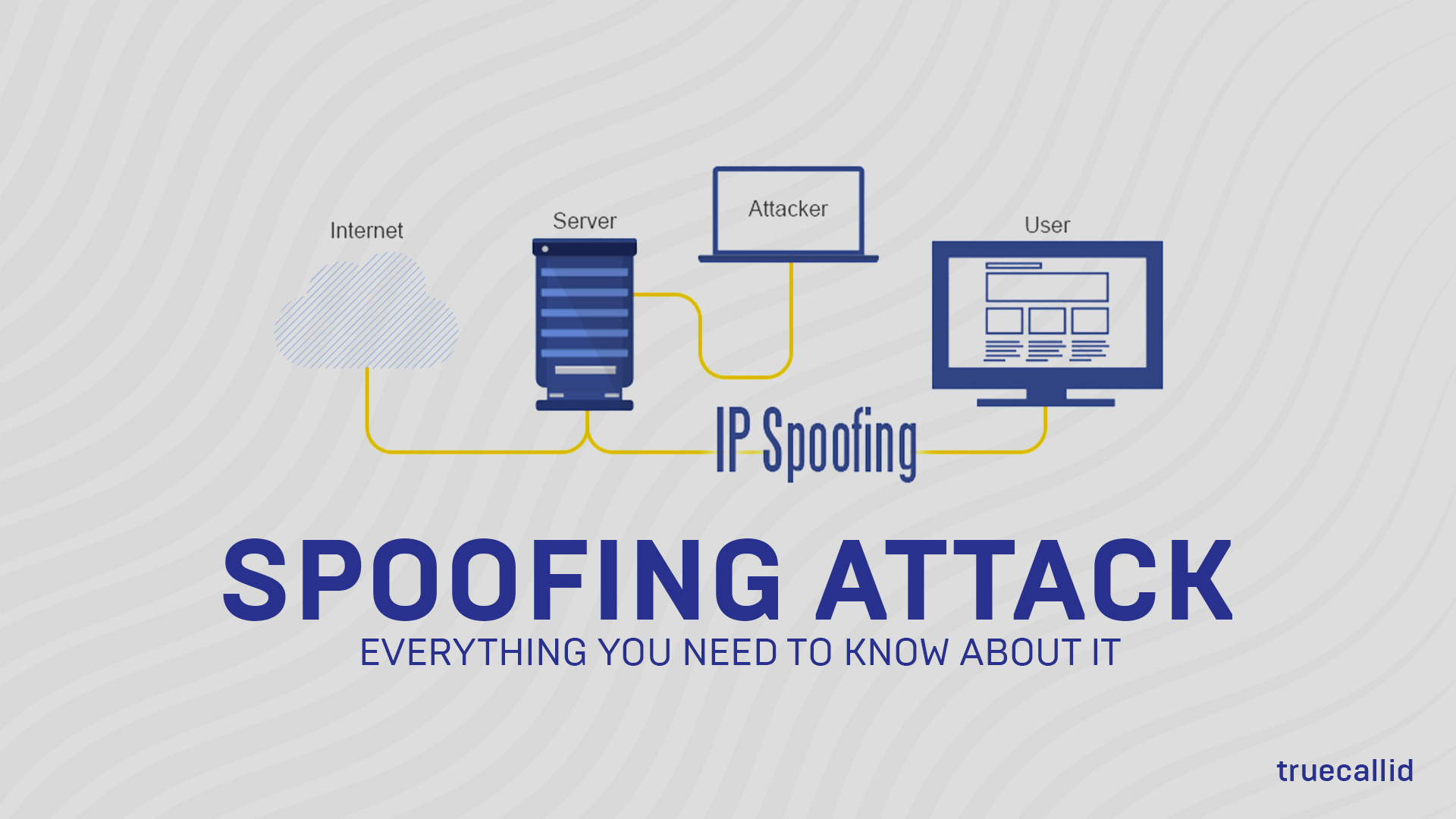
IP SPOOFING:
Security systems verifies any user location by checking out the IP address of the device. Sadly, the fraudulent have the methods to do spoofing attacks on IP address by easily getting safe from the security measures.
TEXT MESSAGE SPOOFING:
Fraudulent parties’ try to spoof attack you by sending you the text message. The expert fraudsters uses different approaches in this kind of spoofing attack, which is harder to judge by anyone.